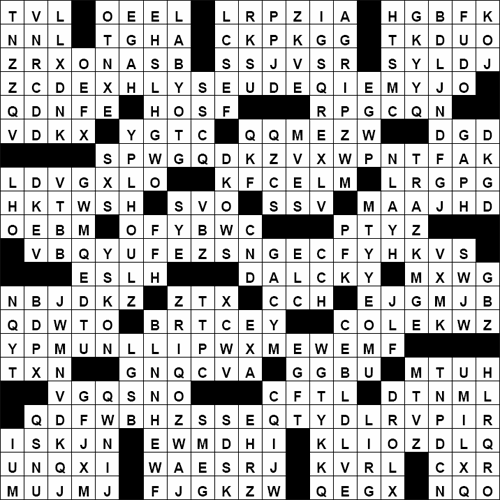
Today, sadly, I had to archive one of my favorite geocache placements – Treasure Hunt.
Why I Archived It
I thought the location would last for a long, long time – in fact, I reused the exact location of the earlier geocache Planes, Trains, and Automobiles which was first hidden in 2003 – I found it in 2007, nearly a year *after* it had been archived.
Since I originally hid the puzzle, its hiding place has become a hotspot for other geocache hiders. When I first hid it, there was plenty of room between it and the next cache. But at the end, it was hidden in pretty much the last available spot in the general area in which it was hidden. I’m sure other people tried to hide a cache nearby – I bet Palmetto had to tell people repeatedly that they couldn’t have their preferred spot due to a puzzle cache final in the vicinity.
Genesis
My goal was to create a truly difficult cache that would nearly require people to work together to solve. Not that a single person wouldn’t have the necessary skills to solve it, just that it would be extraordinarily unlikely that someone would have them all. I have hidden caches of a variety of difficulties, from the very simple to the effort-intensive to the mentally-brutal. This one was supposed to be very tough, aimed at the determined and the collaborative.
The genesis of this idea came when I was doing two things:
- Learning the programming language Java, and
- Solving the New York Times crossword puzzle every day.
The NYT published their puzzle in a format called PUZ that you could download and play with a variety of computer, tablet, and phone apps. It was a very efficient file format.
Unfortunately for the solver, the NYT encrypted the solutions. I believe it was to keep you from getting the answers to easily – I’m sure they wanted to convert bewildered solvers into revenue for the paper by steering the confused towards either calling their for-pay help line or by buying the solution in the paper the next day. So the NYT puzzles had their solutions encrypted, and you weren’t given the decryption key until the next day when the paper came out.
There were two problems with this strategy:
- Crossword enthusiasts had the daily puzzles solved within minutes of publication and would post their own solutions in their blogs.
- The decryption key is only 4-digits long and the PUZ file included a checksum to tell you if your decryption key was correct or not. If that’s confusing to you, don’t worry – the upshot is that a modern desktop computer can find the encryption key for any PUZ file in just a few thousandths of a second.
So the PUZ encryption strategy became more of a hinderance than a help.
At the same time, I was learning Java and thought I could write a better app that would let me play PUZ files than was currently available. I started writing code, and I began by learning to read PUZ files. While there was a PUZ file format document published online, it didn’t give me quite enough detail to understand how to descramble a locked puzzle.
I decided to learn the file format by trying to write my own decoder. And it worked – I found I could write code that would not only read any PUZ file, but I also could generate – and lock or unlock – my own PUZ files. This is made possible by the PUZ file checksum.
A checksum is a quick-and-dirty way to validate a set of data. For instance, suppose I sent you a long list of numbers, and then said that when I added all of those numbers that I got a certain answer. If you take the list of numbers, add the numbers up yourself, and get the same answer that I got, then you’ve got a lot of confidence that the list you received is identical to the list I sent you. That sum is called a checksum – there are many different ways to calculate it, but the idea is ultimately the same.
Every locked PUZ file has a checksum embedded in it. I’ll spare you the mathematical details, but the upshot is this – if you know the ciphertext (which is in the locked PUZ file) and you know the checksum (which is also in the PUZ file), then you can tell if a given unlock code is valid or not (apply the lock code to the ciphertext, then compute the checksum – if they match, the lock code is valid).
Knowing this, I wrote a tool that would read any arbitrary PUZ file, try all possible solutions to unlock it (there are only about 10,000 of them, which is nothing to a modern computer), and then spit out the unlock code as well as an unlocked file. I called my code Jabberwordy and published it without any fanfare as an open-source project.
At about this same time, I was working my way through a book of crossword puzzles titled Will Shortz’s Favorite Sunday Crossword Puzzles and came upon the puzzle “Treasure Hunt” by one of the best constructors in the field today: Patrick Berry. It’s a great puzzle – you should find it and try solving it yourself.
That’s when it hit me: what if I created a geocache that used the PUZ encryption algorithm to hid the coordinates? And thus, the Treasure Hunt geocache was born.
The Solution
My challenge with Treasure Hunt was this: how do I get people to figure out that they’re supposed to use the PUZ file encryption without saying that explicitly? I did this in a few ways:
- The Related Web Page link on the cache page points to a PUZ file for the Patrick Berry “Treasure Hunt” crossword. Most solvers (I think?) discovered this.
- The image in the description shows a crossword grid with random letters in it. The grid in the image is identical to the grid the unlocked PUZ file from the link. That implied that the two were related somehow.
Now, it’s time to go into a bit of technical detail about the PUZ file format. In a PUZ file, the letters in the solution are listed in order, left-to-right, and the black squares are marked as period (.) characters. So if you open a PUZ file, you can read the across entries of the solution pretty easily.
However, when a PUZ file is encrypted, each letter is converted into a new letter using what amounts to a polyalphabetic cipher (see Puzzle Solving 101 #7 for details on these). Applying the 4-digit unlock code for the PUZ file will convert the cleartext to ciphertext, and if you apply it again, it converts the ciphertext back to cleartext.
For folks that figured out that the unlock code was important (and multiple people did), I threw in another hint – the PUZ file you could download was not identical to the one you could download from the NYT. In fact, if you figured out or guessed the unlock code for that file (and multiple people did), you would end up not with the solution to Patrick Berry’s original puzzle, but the text to the grid in the image in the description. That should have been a really strong hint for the next step.
The Aha Moment
If you got this far, I expected that you would make the big leap to what would ultimately lead you to the solution – that the text in the image was actually the ciphertext for the PUZ file, not the cleartext. Those seemingly random letters – reading left-to-right T, V, L, ., O, E, E, L, etc – were actually the cipher text of the PUZ file. Your job as the puzzle solver was to realize that you had to create a PUZ file where the letters in the given grid were the ciphertext.
But what about the checksum? That’s the number in the cache hint: 53878.
So to solve the puzzle you had to build a PUZ file with the given ciphertext and checksum, find the unlock code for that file, then read out the solution from the cleartext. It sounds so easy that way, and yet baffled a lot of people for a long time.
The Prose
Figuring out the file format part was supposed to be the tough part. If you got through that, I didn’t want you to have to suffer too much more.
But I did want you to suffer somewhat. I didn’t want to make the puzzle just a simple matter of cracking the code and then getting the coordinates to the solution. In fact, the solution never actually gives you the longitude and latitude of the cache.
Instead, the solution is to read the letters in the unlocked grid in top-to-bottom order, then left-to-right order. I did this to keep it from being too obvious from the PUZ file, since the PUZ file contains the letters in across order, not down order.
So, the letters you end up with reading them in down order are:
CONGRATSYOUHAVESOLVE
DTHECODENOWGOFINDTHE
MOTHERLODETWISTSANDT
URNSYOUHAVETOMAKESTA
RTSEARCHINGTERRAPINS
LAKEYOUWILLSURELYPAS
STHETESTFINDACERTAIN
MICAPESTMANYSPOTSARE
INTHEGRIDSTANDUPONTH
ESPOTGETHIDTRAVELTWE
NTYPACESSOUTHTOTHETU
NATRAILERMOUTHTURNLE
FTTOTHEDESTINATIONPA
SSTIARABOTHERSTATION
GOAHEADFORNINETYFEET
GARTERSFLINGONSPRYSE
CRETELOOKBEHINDTHEFI
NALSTAGEFORTHEMETALE
CHOCAGE
If you try reading that out loud, you’ll notice some of the words rhyme and that there seems to be a rhythm to reading them. Which isn’t an accident – it’s a hint that you need to break up this text into rhyming couplets, like so:
CONGRATS YOU HAVE SOLVED THE CODE
NOW GO FIND THE MOTHER LODETWISTS AND TURNS YOU HAVE TO MAKE
START SEARCHING TERRAPINS LAKEYOU WILL SURELY PASS THE TEST
FIND A CERTAIN MICA PESTMANY SPOTS ARE IN THE GRID
STAND UPON THE SPOT GET HIDTRAVEL TWENTY PACES SOUTH
TO THE TUNA TRAILER MOUTHTURN LEFT TO THE DESTINATION
PASS TIARA BOTHER STATIONGO AHEAD FOR NINETY FEET
GARTERS FLING ON SPRY SECRETELOOK BEHIND THE FINAL STAGE
FOR THE METAL ECHO CAGE
But that still doesn’t make literal sense – there is no place in Broward County called TERRAPINS LAKE. (Trust me – I checked, just in case.)
But there is a place nearby called EASTERLIN PARK, which is an anagram of TERRAPINS LAKE. (And there are, in fact, terrapins in the lake in Easterlin Park.) So if you anagram the confusing ends of each couplet, you get directions to find the final location – just like the themed entries gave you directions to find the solution in Patrick Berry’s original “Treasure Hunt” crossword. So the real solution is:
CONGRATS YOU HAVE SOLVED THE CODE
NOW GO FIND THE MOTHER LODETWISTS AND TURNS YOU HAVE TO MAKE
START SEARCHING EASTERLIN PARK [TERRAPINS LAKE]YOU WILL SURELY PASS THE TEST
FIND A CERTAIN CAMP SITE [MICA PEST]MANY SPOTS ARE IN THE GRID
STAND UPON THE SPOT [CAMP SITE] D-EIGHT [GET HID]TRAVEL TWENTY PACES SOUTH
TO THE NATURE TRAIL [TUNA TRAILER] ENTRANCE [MOUTH]TURN LEFT TO THE DESTINATION
PASS [THE SIGN MARKED] HABITAT RESTORATION [TIARA BOTHER STATION]GO AHEAD FOR NINETY FEET
STRANGLER FIG [GARTERS FLING] ON CYPRESS TREE [SPRY SECRETE]LOOK BEHIND THE FINAL STAGE
FOR THE METAL GEOCACHE [ECHO CAGE]
So if you go to Easterlin Park, find camp site D-8, stand on the “D-8” on the road at that camp site, walk 20 paces south to the signed entrance to the nature trail, go in and immediately go left, go to the sign that reads “Habitat Restoration”, walk 90 paces beyond that to the giant cypress tree on the left being overrun by a strangler fig, then look behind it, you’ll find the hiding spot.
The folks who figured this out were absolutely brilliant in using rhyming couplets in their log entries.
The Final Hint
I did want this one to be tough, but I didn’t want it to be completely unsolvable. So I decided to release a hint after what I thought was a sufficient amount of time (which turned out to be 18 months after publication). The log entry at that link is both an honest letter as well as a hint – the initial letters of each paragraph in the hint spell PUZ ENCRYPTION, which was all it took for folks to crack the rest open.
Congrats to everyone who solved it! (And apologies to harper117 who cracked the puzzle after the cache had been muggled.)